Documentation
Presentation
SSH Tunnel Manager is a macOS application to manage SSH tunnels. If you don't know what SSH tunnels are, you can read more about them here or in the man page in the -L and -R sections. Here is how the man page describes it. Keep in mind these are arguments to the ssh commands, so they work in the context of a SSH connexion to a remote host you have access to.
-L local redirects
Specifies that connections to the given TCP port or Unix socket on the local (client) host are to be forwarded to the given host and port, or Unix socket, on the remote side. This works by allocating a socket to listen to either a TCP port on the local side, optionally bound to the specified bind_address, or to a Unix socket. Whenever a connection is made to the local port or socket, the connection is forwarded over the secure channel, and a connection is made to either host port hostport, or the Unix socket remote_socket, from the remote machine. Port forwardings can also be specified in the configuration file. Only the superuser can forward privileged ports. IPv6 addresses can be specified by enclosing the address in square brackets. By default, the local port is bound in accordance with the GatewayPorts setting. However, an explicit bind_address may be used to bind the connection to a specific address. The bind_address of “localhost” indicates that the listening port be bound for local use only, while an empty address or ‘*’ indicates that the port should be available from all interfaces.
-R remote redirects
Specifies that connections to the given TCP port or Unix socket on the remote (server) host are to be forwarded to the given host and port, or Unix socket, on the local side. This works by allocating a socket to listen to either a TCP port or to a Unix socket on the remote side. Whenever a connection is made to this port or Unix socket, the connection is forwarded over the secure channel, and a connection is made to either host port hostport, or local_socket, from the local machine. Port forwardings can also be specified in the configuration file. Privileged ports can be forwarded only when logging in as root on the remote machine. IPv6 addresses can be specified by enclosing the address in square brackets. By default, TCP listening sockets on the server will be bound to the loopback interface only. This may be overridden by specifying a bind_address. An empty bind_address, or the address ‘*’, indicates that the remote socket should listen on all interfaces. Specifying a remote bind_address will only succeed if the server's GatewayPorts option is enabled (see sshd_config(5)). If the port argument is ‘0’, the listen port will be dynamically allocated on the server and reported to the client at run time. When used together with -O forward the allocated port will be printed to the standard output.
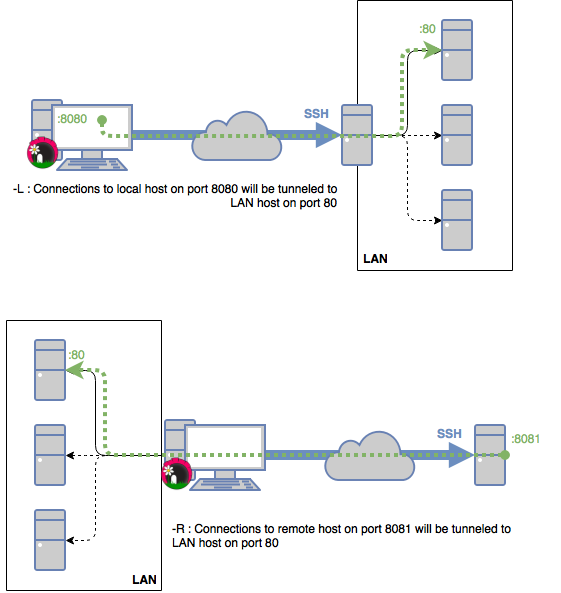
Local and Remote tunnels
The following schema explains the main difference between a local tunnel (-L in SSH command line) and a remote tunnel (-R in SSH command line).
To put it shortly, local tunnels lets you connect to another computer distant from you, while remote tunnels lets people distant from you connect to your local LAN.
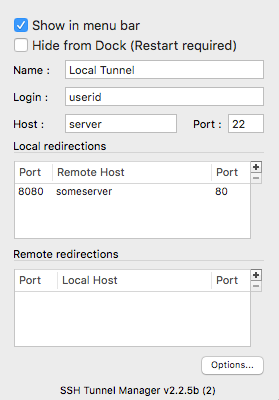
The configuration for the situation on the top would be as follow :
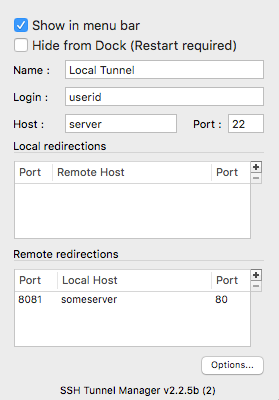
The configuration for the situation on the bottom would be as follow :
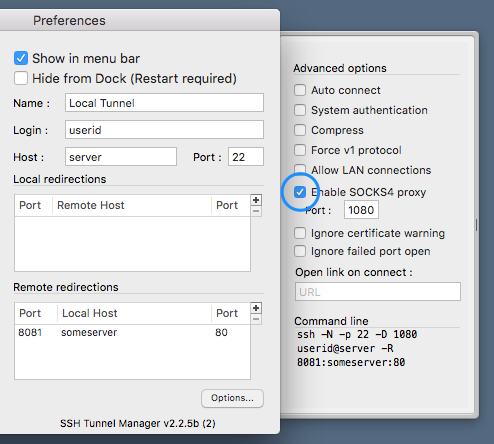
SOCKS proxy
All of this seems pretty cool, but wouldn't it be even cooler if we could just tunnel any trafic to the remote host to make it as if we were browsing from that host?
Thanks to the SOCKS protocol and SSH, you can configure a SSH connection to open a SOCKS proxy on your local computer. Once you have done that, you just have to inform the system to use SOCKS proxy on localhost:1080 (by default).
This is how you configure it in your system, going to System Preferences > Network > Advanced
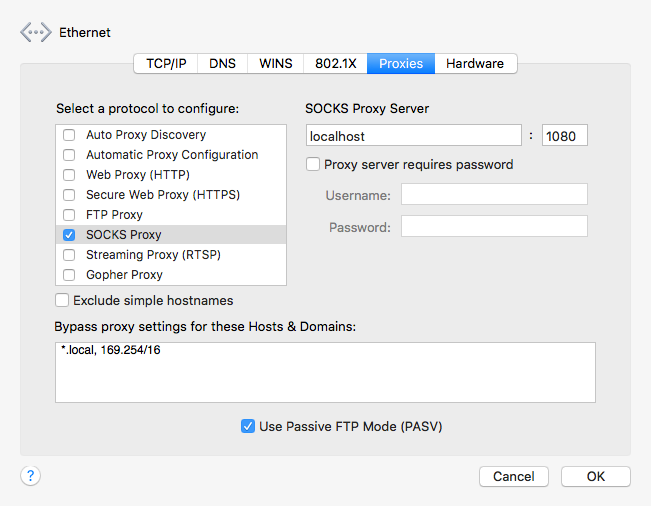
Now any application that honors SOCKS proxy settings will be using the tunnel for their network activity. It will be the case for most web browser, Apple Mail, etc...